Securing Digital Evidence for Law Enforcement: Integrity & Custody
By Umair Ahmad on Nov 23, 2024 10:00:00 AM

Picture this: a critical criminal case hinges on digital evidence containing a trail of emails, phone records, surveillance footage, and geolocation data from the suspect’s device. You’ve carefully gathered all of it, but one mistake in handling one minor breach in the chain of custody and that could be the difference between a conviction and a mistrial.
The defense will jump at the opportunity to challenge the integrity of evidence, potentially throwing your investigation into jeopardy.
For law enforcement officers, forensic investigators, and digital evidence managers, securing digital evidence is not just about collecting rather it’s about ensuring its integrity and preserving its admissibility in court.
The complexity and volume of digital evidence in today’s criminal investigations only magnify the challenges agencies face trying to prevent any breaks in the chain. As technology advances, so does the sophistication of the criminals use it. However, in the race to keep up, it’s easy to overlook the simple yet critical procedures that ensure maintaining evidence integrity.
In this post, we’ll walk through the most pressing challenges of securing digital evidence, why maintaining the chain of custody is non-negotiable, and how modern tools such as Digital Evidence Management Systems (DEMS) that can safeguard your evidence from compromise, ensuring it remains legally defensible in court.
The Growing Role of Digital Evidence in Criminal Investigations
As technology becomes more embedded in daily life, digital evidence has emerged as a vital element in modern investigations. From emails to cloud data, its role is no longer optional but essential requirement to proper handling, analysis, and security to support effective case outcomes.
The Critical Role of Digital Evidence
Much evidence is stored electronically in the digital age, from text messages and social media posts to database entries, cloud storage, and even IoT devices. Digital evidence has become indispensable in solving everything from cybercrimes to traditional crimes where technology plays a role, such as hacking, identity theft, and even violent crimes involving digital footprints.
With this expansion comes an inherent problem: digital evidence is highly susceptible to tampering, corruption, and loss if improperly handled. Cybersecurity risks and the potential for human error make it more difficult than ever to ensure that evidence remains intact throughout an investigation.
A study by the National Institute of Justice found that in most cases, digital evidence plays a role in securing convictions, especially in cases involving fraud, theft, or any form of online criminal activity. In many instances, the forensic examination of hard drives, phones, and emails proves to be the smoking gun.
Types of Digital Evidence in Criminal Investigations
Digital evidence is broadly categorized, and it can be found in various forms:
- Cloud Storage: As more users move their data to the cloud, accessing evidence stored remotely has become increasingly complex. Cloud-based platforms like Google Drive, OneDrive, and iCloud store critical documents, email communications, and backups that investigators need to access.
- Social media & Online Accounts: Social media platforms like Facebook, Twitter, and Instagram, along with messaging platforms like WhatsApp, hold massive volumes of data, including direct messages, photos, location check-ins, and timestamps. Extracting this data correctly is critical for a successful investigation.
- IoT Devices & Smart Home Technology: From smartwatches and fitness trackers to security cameras and smart speakers, these devices generate data that can provide crucial insights into criminal activities. However, accessing and managing this evidence comes with challenges related to security and data extraction.
Digital evidence is vast and diverse and often volatile meaning that improper handling can permanently alter or even delete data. With each new form of digital evidence, the stakes get higher, and the margin for error grows smaller.
The Chain of Custody: The Lifeline of Digital Evidence
Maintaining the integrity of digital evidence hinges on a well-documented chain of custody. As digital files are easily altered, ensuring clear, continuous tracking from collection to courtroom is critical for preserving their admissibility and credibility.
What is the Chain of Custody?
At its core, the chain of custody is the documentation that tracks the possession, handling, and location of evidence from the moment it is collected until it is presented in court. The purpose is simple: to ensure the evidence remains unaltered and uncorrupted by any outside influence during its lifecycle.
A robust chain of custody establishes that the evidence you present in court is the same evidence collected during the investigation. Without it, the integrity of the evidence is called into question. Even the appearance of a break in the chain can render the evidence inadmissible.
The Key Elements of Chain of Custody
To maintain the chain of custody, law enforcement must ensure:
- Proper Documentation: Every piece of evidence must be documented with specific details, including who collected it, where it was found, the date and time of collection, and who handled it subsequently.
- Secure Storage: Evidence must be stored in a secure location, typically a forensic storage facility or a tamper-proof environment that restricts unauthorized access.
- Audit Trails: Every time the evidence is transferred or accessed, it should be logged and monitored. This ensures no unauthorized individuals are interacting with the evidence.
- Evidence Transfer Logs: When evidence changes hands, it’s vital to have a transfer log indicating who received the evidence, the date, and the purpose of the transfer.
Challenges in Maintaining the Chain of Custody
While the principle is clear, executing it precisely is far more complex. Law enforcement agencies face several challenges:
- Human Error: A missing signature, incorrect documentation, or an unrecorded handoff can create gaps in the chain of custody. This is one of the most common causes of evidence mishandling.
- Manual Tracking Systems: Many law enforcement agencies still rely on manual logs or paper-based systems for tracking evidence. These systems are prone to inaccuracies, discrepancies, and the potential for miscommunication.
- Multi-Agency Coordination: In cases involving multiple jurisdictions or agencies, evidence may be handed off several times, leading to confusion and the potential for missed documentation.
These risks highlight the importance of a secure, transparent, and automated system for tracking digital evidence.
The Consequences of Mishandling Digital Evidence
If digital evidence isn’t handled correctly, it can cause big problems. Even small mistakes can lead to the evidence being thrown out, letting the wrong person go free or making people lose trust in the police.
Breaking the Chain of Custody
Any break in the chain of custody can have serious repercussions:
- Exclusion of Evidence: If the defense can show that the evidence was not handled properly, it may be excluded from the case entirely, leaving investigators without their primary source of proof.
- Wrongful Acquittals or Convictions: Mishandling of evidence can lead to wrongful convictions or acquittals, potentially allowing the guilty to go free while the innocent suffer.
- Reputational Damage to Law Enforcement: Failure to protect evidence can damage the credibility of the agency involved, eroding public trust and potentially compromising future cases.
A glaring example of this was the infamous O.J. Simpson trial, where evidence-handling mistakes played a significant role in the defense’s success in casting doubt on the integrity of the evidence. The mishandling of a critical bloody glove and failure to maintain the chain of custody of key items led to reasonable doubt, which the defense exploited.
The Growing Complexity of Digital Evidence
As technology evolves, so does the complexity of digital evidence. Investigators must keep pace with new storage devices, encrypted data, and remote access methods that complicate the process of securing evidence. In the past, a physical piece of evidence such as, a weapon was relatively easy to protect. Today, however, investigators are tasked with securing data from cloud servers, encrypted drives, and even the dark web, all of which require specialized knowledge and tools.
Best Practices for Securing Digital Evidence
To keep digital evidence safe, there are smart steps that police and investigators need to follow. If they collect, store, and track the evidence the right way, it stays safe and useful in court. Using the right tools and staying updated through training helps make sure nothing gets lost or changed by mistake.
1. Proper Collection and Documentation
The foundation of securing digital evidence starts with its collection. Here’s what needs to be done:
- Forensically Sound Collection: Ensure that the collection process doesn’t alter the evidence. This includes using write-blockers when extracting data from hard drives and ensuring that data integrity checks (hashing) are performed immediately after collection.
- Thorough Documentation: Every step of the collection and handling process should be documented. This documentation must include the chain of custody log, detailing who handled the evidence, when, and where it was stored.
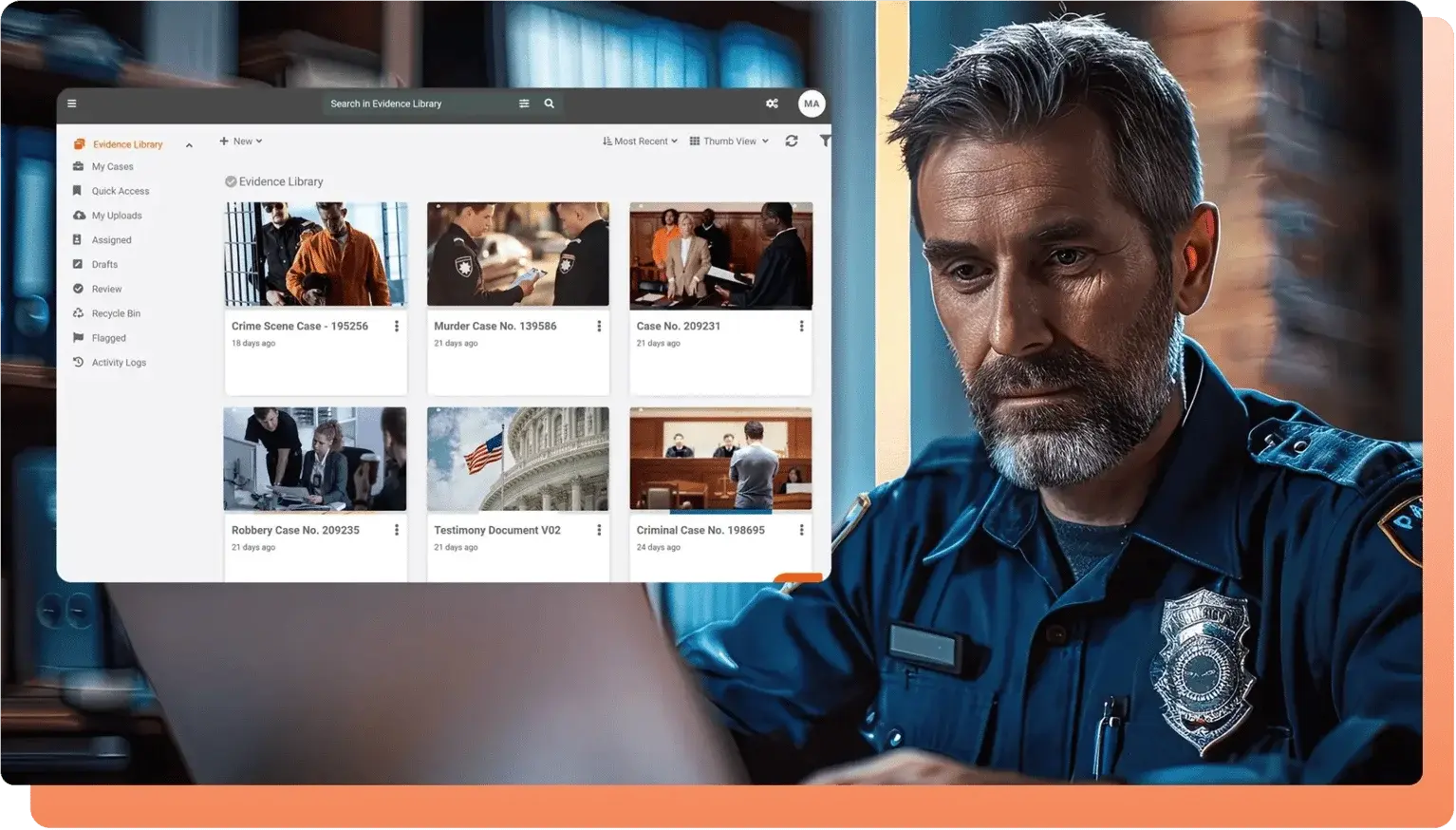
Best Practice Tip: Utilize Digital Evidence Management Systems (DEMS) to automate this process. These systems can ensure real-time tracking and prevent errors.
2. The Role of Digital Evidence Management Systems (DEMS)
A Digital Evidence Management System (DEMS) can be a game-changer in ensuring the integrity of evidence and maintaining a seamless chain of custody. These systems can:
- Automate Evidence Tracking: Every time evidence is handled, the system automatically logs the action, preventing human error.
- Centralized Evidence Storage: Secure storage systems, often cloud-based, allow for safe, encrypted storage of digital evidence. With audit trails, it’s easy to track who accessed the data and when.
- Chain of Custody Management: DEMS software helps track evidence from collection to courtroom, ensuring that all actions taken are transparent and verifiable.
Best Practice Tip: Look for a DEMS with built-in encryption, access control, and real-time tracking to safeguard data integrity.
3. Secure Storage and Encryption
Once evidence is collected, securing it becomes a top priority. Store evidence in an airtight system whether physical or digital that restricts unauthorized access. This is especially critical for cloud storage solutions. Data should be encrypted both at rest and in transit.
Best Practice Tip: Use AES-256 encryption for evidence storage and ensure that multi-factor authentication (MFA) is required for accessing sensitive data.
4. Ongoing Training and Awareness
Digital forensics is a constantly evolving field, and ongoing training is crucial. Law enforcement officers, forensic investigators, and evidence managers must be regularly trained on:
- The latest tools for digital evidence extraction and data analysis.
- Proper evidence handling and documentation protocols.
- Emerging threats to data integrity, including the risks of data tampering and cyberattacks.
Best Practice Tip: Regularly schedule cybersecurity awareness training and workshops to ensure that all personnel are aware of the latest tactics used by criminals to destroy or corrupt digital evidence.
Key Takeaways
-
Digital Evidence Is Crucial in Modern Investigations: With the increasing role of technology in criminal activity, securing digital evidence like emails, phone records, and IoT data has become essential in solving crimes and securing convictions.
-
The Chain of Custody Ensures Integrity: Maintaining an unbroken chain of custody is vital to preserving the integrity and admissibility of digital evidence in court. Documentation, secure storage, and audit trails are key to ensuring evidence remains untampered with.
-
Leverage Digital Evidence Management Systems (DEMS): DEMS automate evidence tracking, provide centralized storage, and ensure secure handling. Look for systems with built-in encryption, access control, and real-time tracking to maintain evidence integrity.
-
Encryption Protects Evidence: Encrypting data with robust standards like AES-256 ensures digital evidence is secure both at rest and in transit. It prevents unauthorized access, tampering, or breaches throughout the evidence lifecycle.
-
Ongoing Training Is Essential: Regular training on proper evidence handling, the latest forensic tools, and emerging cybersecurity threats is crucial for law enforcement officers and digital evidence managers to maintain data integrity.
-
Documentation and Audit Trails Are Key: Proper documentation detailing who handled the evidence, when, and why is it crucial to maintaining an effective chain of custody. Automated audit trails ensure transparency and help prevent mishandling.
-
Secure Storage and Access Controls: Evidence must be stored in a secure, tamper-proof system, with restricted access to authorized personnel only. Multi-factor authentication (MFA) and encrypted storage are crucial for safeguarding sensitive data.
-
Handling New Evidence Forms: As technology evolves, so does the complexity of digital evidence. Specialized tools and knowledge are required to handle emerging types of evidence, like data from IoT devices, encrypted drives, and cloud-based platforms.
Ensuring Justice by Securing Digital Evidence
The future of criminal investigations is digital, and as more crimes are committed using technology, securing digital evidence and maintaining an unbroken chain of custody is more important than ever. Mishandling digital evidence not only jeopardizes individual investigations but can have widespread consequences for the credibility of law enforcement agencies.
By embracing best practices, utilizing Digital Evidence Management Systems, and focusing on continuous training, law enforcement can ensure that the digital evidence they rely on remains intact, secure, and legally defensible.
People Also Ask
What is digital evidence, and why is it important?
Digital evidence refers to data stored or transmitted electronically, such as emails, social media posts, and mobile device data. It's critical because it often provides the evidence needed to solve crimes.
What are the best practices for collecting digital evidence?
Best practices include ensuring the evidence is collected without alteration, maintaining comprehensive documentation, and following forensic guidelines to preserve data integrity.
Why is the chain of custody important?
The chain of custody ensures that digital evidence remains untampered with and legally admissible. It provides a transparent record of who handled the evidence and when.
How can digital evidence be protected in court?
Protecting digital evidence in court requires maintaining a solid chain of custody, using encryption, and ensuring that the evidence remains unchanged throughout the investigation and trial.
What tools are available to help secure digital evidence?
Tools like Digital Evidence Management Systems (DEMS), write-blockers, and data encryption technologies ensure evidence remains secure and tamper-proof.
What should law enforcement do if they suspect evidence tampering?
Law enforcement should immediately document the tampering, notify supervisors, and take steps to secure any remaining evidence. They should also initiate a formal investigation into the tampering incident.
What are the consequences of mishandling digital evidence?
Mishandling digital evidence can lead to the exclusion of crucial evidence, wrongful convictions or acquittals, and reputational damage to law enforcement agencies.
How can cloud-based evidence storage improve evidence management?
Cloud-based storage allows for scalable, secure, and easily accessible evidence storage, with built-in encryption and audit logs that help maintain evidence integrity.
What role does encryption play in securing digital evidence?
Encryption ensures that unauthorized parties cannot access or alter digital evidence, protecting its integrity during storage and transfer.
How can training improve digital evidence management?
Regular training helps law enforcement stay updated on the latest tools and protocols for handling digital evidence, ensuring that everyone involved in the process understands their responsibilities.
Jump to
You May Also Like
These Related Stories
Digital Evidence Management System Guide for Law Enforcement

How On-Premises Digital Evidence Management Software for Counties Cuts Long-Term Costs





No Comments Yet
Let us know what you think