Ensuring Digital Evidence Preservation: Safeguard Against Legal Risks
By Bassam Mazhar on Nov 20, 2024 8:50:45 AM, ref:

Discover best practices for secure digital evidence management and preservation to protect your organization from legal risks.
Protecting the integrity of digital evidence is critical for any organization involved in investigations, audits, or legal proceedings. Even a small error in how evidence is collected, stored, or handled can jeopardize an entire case—and in many situations, lead to evidence being rejected in court.
Imagine building a solid case only to see it fall apart because a file was mishandled, metadata was altered, or the chain of custody wasn’t documented correctly. These risks are very real for compliance teams, IT security managers, and legal departments. Poor digital evidence preservation not only weakens legal outcomes but also puts your organization’s reputation and security at stake.
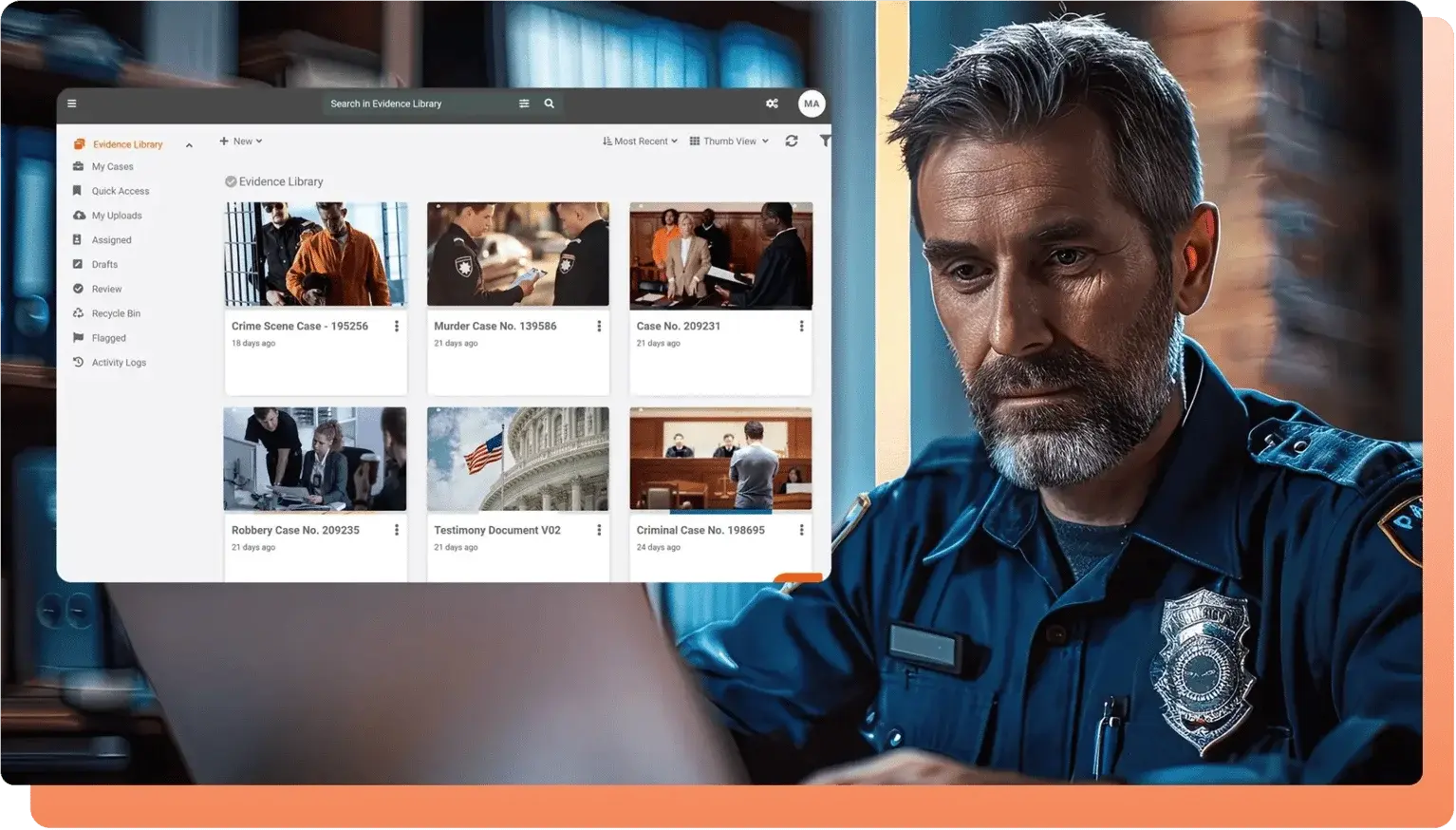
Effective evidence preservation requires more than saving files on a server. It demands strict processes, secure technology, and a deep understanding of how digital data can be corrupted, tampered with, or legally challenged. Organizations must use the right tools—such as a secure Digital Evidence Management System (DEMS)—to ensure evidence stays authentic, verifiable, and admissible.
In this blog, we’ll break down the key challenges in digital evidence preservation, explore best practices for secure collection and storage, and show how organizations can safeguard digital evidence against tampering, loss, and legal risks.
Understanding Digital Evidence and Its Importance
Digital evidence refers to any information stored, processed, or transmitted in digital form that can support an investigation or legal proceeding. This can include emails, text messages, call logs, social media posts, documents, surveillance footage, body-cam videos, GPS data, and metadata from servers or databases.
Because digital interactions leave detailed, time-stamped records, digital evidence has become essential in criminal and civil cases, corporate investigations, HR disputes, cybersecurity incidents, and regulatory audits. Its ability to provide objective, verifiable insights makes it one of the most powerful forms of modern evidence—provided it is collected and preserved correctly.
For digital evidence to be admissible in court, it must meet strict legal, forensic, and data protection requirements, including frameworks such as GDPR, CJIS, and jurisdiction-specific evidence laws. To be considered reliable, the evidence must clearly demonstrate that:
- Data integrity is preserved — the evidence has not been altered, corrupted, or tampered with.
- A complete and transparent chain of custody exists — every access, transfer, or action taken on the evidence is fully documented.
- Storage is secure and controlled — ensuring the evidence is protected against unauthorized access, data loss, or accidental modification.
Failure to meet these standards can result in the evidence being ruled inadmissible, undermining legal cases and investigations. In corporate environments, mishandling digital evidence can lead to regulatory penalties, compliance violations, financial losses, and significant reputational damage.
Effective Digital Evidence Management is therefore not optional—it is essential for maintaining trust, ensuring legal defensibility, and protecting organizational integrity.
The Complexities of Digital Evidence Collection and Preservation
The National Institute of Health (NIH) reports that digital evidence volumes are accelerating due to the widespread use of digital devices and their critical role in legal cases. Managing this vast array of digital information, however, is challenging:
- Decentralized Data: Digital evidence can originate from various sources, including mobile devices, email, surveillance systems, cloud storage, and other sources. Collecting and centralizing this evidence securely is essential to ensure that no crucial data is lost.
- Legal Compliance Requirements: Every region or country has specific guidelines for evidence handling, and any deviation could result in the dismissal of evidence.
- Security Risks: Digital evidence is highly sensitive and prone to unauthorized access, tampering, or accidental deletion, all of which can impact its credibility and admissibility.
- Volume and Format Diversity: Digital evidence often exists in different formats (e.g., images, audio files, emails, texts), creating a significant burden on forensic teams who must sift through vast amounts of information to identify relevant data.
Therefore, organizations require a robust and systematic approach to collecting and preserving digital evidence to navigate these complexities and avoid legal consequences, financial losses, and reputational damage.
A Step-By-Step Guide to Secure Digital Evidence Collection and Preservation
How can you ensure proper handling of every digital asset, from video footage to email records? Let’s break down the steps to creating a foolproof digital evidence process.
Step 1: Establish a Digital Evidence Policy
A Digital Evidence Policy serves as the foundation for any evidence management process. This policy should be a comprehensive document outlining how digital evidence is identified, collected, accessed, stored, and retained within the organization.
Essential Components of a Digital Evidence Policy:
- Types of Digital Evidence: Define what constitutes digital evidence (emails, videos, internal messages, logs, etc.).
- Access Permissions: Outline permissions and protocols for each user role within the organization.
- Retention and Disposal: Specify how long evidence should be retained and when or how it should be securely disposed of.
Establishing a Digital Evidence Policy provides a consistent approach to handling evidence and creates accountability standards for everyone involved.
Step 2: Use a Chain of Custody Protocol
The chain of custody is crucial for the admissibility of evidence. It involves tracking every interaction with the evidence, from collection to presentation, to prove that it has remained unaltered. A secure chain of custody ensures that no unauthorized individuals have accessed, modified, or tampered with the evidence.
Critical Elements of a Chain of Custody Protocol
- Detailed Logs: Document each interaction, including access, copying, and any modifications made.
- Timestamping: Timestamp each entry for maximum clarity.
- User Identification: Identify each individual accessing the evidence.
A secure, automated solution simplifies this process. An advanced digital evidence management software provides a built-in chain of custody tracking, giving you a clear, tamper-proof log of all actions taken with each piece of evidence and effectively allowing you to preserve digital evidence.
Step 3: Ensure Evidence Integrity with Digital Hashing
Maintaining data integrity is crucial to preserving the credibility of digital evidence. Digital hashing or tamper detection capabilities are one of the most reliable methods for ensuring data integrity.
Tamper detection allows for the hashing of digital evidence when it’s collected, and then re-verifies the hashes when access is made, helping to demonstrate that the evidence remains unchanged. VIDIZMO’s platform supports automatic hashing for each piece of evidence, ensuring consistency without manual checks.
Step 4: Store Evidence in a Secure, Centralized Platform
Storing digital evidence securely is just as crucial as collecting it securely. Here are a few essential storage principles:
- Encryption: Encrypt data both at rest and in transit. This setup prevents unauthorized access even if someone intercepts the data.
- Access Controls: Limit access based on roles. Only authorized individuals should be able to view or interact with evidence.
- Regular Backups: Data loss is catastrophic for evidence preservation. Regular backups ensure evidence is recoverable even in cases of system failure.
Step 5: Automate Evidence Collection Wherever Possible
Automation is invaluable for reducing the risk of human error in evidence collection. From recording to secure digital evidence storage, automated systems can minimize the chances of accidental tampering or loss.
Advanced digital evidence management solutions automatically ingest, log, and store evidence in a compliant manner. This removes many manual touchpoints where errors or missteps might occur.
Strengthen Legal Integrity with Effective Digital Evidence Management
By correctly managing digital evidence collection and preservation, your organization can safeguard its integrity, reputation, and legal standing. Following a structured process that includes setting policies, ensuring a robust chain of custody, maintaining data integrity, secure storage, and automating processes where possible is essential.
Advanced Digital Evidence Management Solutions, such as those incorporating AI-driven features, enable organizations to handle digital evidence with precision and security. These solutions protect against accidental tampering, unauthorized access, or broken chains of custody, allowing legal teams to focus on building strong, defensible cases.
Key Takeaways
-
Digital Evidence Matters
Digital evidence—emails, videos, documents, metadata, social media content—is essential in legal cases and corporate investigations, and must be preserved correctly to remain admissible. -
Protecting Integrity is Critical
Tamper detection, hashing, and strong encryption during storage and transit ensure digital evidence remains authentic and secure from unauthorized access. -
Chain of Custody Is Non-Negotiable
A fully documented chain of custody proves who accessed the evidence, when, and why—ensuring it has not been altered or compromised. -
Centralized & Secure Storage
Storing evidence in a centralized, encrypted platform with role-based access controls ensures confidentiality and prevents unauthorized interaction. -
Automation Improves Accuracy
Automated evidence capture through an advanced Digital Evidence Management System (DEMS) reduces human error, logs all actions, and simplifies compliance. -
Legal Compliance Must Be Maintained
Adhering to standards such as GDPR, CJIS, and the Federal Rules of Evidence ensures digital evidence is preserved legally and defensibly. -
Backup & Recovery Are Essential
Regular encrypted backups and redundant storage prevent data loss, ensuring digital evidence can always be recovered when needed.
Secure Digital Evidence Management
Proper digital evidence management is no longer a back-office task but rather a foundational requirement for organizations aiming to stay legally protected and operationally sound. From initial collection to long-term preservation, every step must be deliberate, secure, and defensible.
Investing in advanced digital evidence management tools empowers teams to work more efficiently while maintaining the highest standards of integrity and compliance. Features like automated ingestion, hashing, and encryption not only simplify processes but also instill confidence in the validity of the evidence.
In a world where digital incidents can escalate quickly, being prepared is everything. By implementing structured, tamper-proof systems, organizations can protect their reputation, mitigate legal risks, and uphold the truth, no matter what challenges arise.
People Also Ask
What is digital evidence, and why is it important?
Digital evidence includes electronically stored information—such as emails, texts, videos, or server logs—used in legal or investigative processes. It’s important because it provides verifiable, time-stamped data that can support or challenge claims in court or audits.
What is digital evidence collection, and how is it done securely?
Digital evidence collection involves identifying, acquiring, and documenting data from sources like mobile devices, servers, or surveillance systems. Secure collection requires encryption, minimal manual handling, automated tools, and a strict chain of custody to avoid tampering or data loss.
What is the chain of custody in digital evidence preservation?
The chain of custody is a detailed record of every interaction with a piece of digital evidence—who accessed it, when, and what actions were performed. It ensures the evidence remains authentic and admissible in court.
Why is secure digital evidence management essential for organizations?
Secure digital evidence management protects sensitive data from tampering, unauthorized access, or accidental loss. It also helps organizations comply with standards like GDPR, CJIS, and the Federal Rules of Evidence while reducing legal and regulatory risks.
What are the best practices for digital evidence preservation?
Key best practices include using a formal evidence policy, encrypted storage, automated ingestion, tamper detection through hashing, maintaining a complete chain of custody, and enforcing strict role-based access controls.
How does tamper detection support digital evidence integrity?
Tamper detection uses cryptographic hashing to confirm that evidence has not been modified. Matching the original hash with the current one validates authenticity, which is essential for legal admissibility.
What role does automation play in managing digital evidence?
Automation reduces human error by automatically ingesting, tagging, and storing evidence. It improves consistency, ensures accurate audit trails, and strengthens compliance across large volumes of digital data.
Why is centralized digital evidence storage recommended?
Centralized storage keeps all evidence encrypted, backed up, and access-controlled within one secure platform. It simplifies retrieval, improves collaboration, and provides a single source of truth.
How can an organization meet compliance requirements in evidence handling?
Organizations can meet compliance requirements by using Digital Evidence Management Systems (DEMS) that maintain chain of custody, enforce access controls, enable tamper detection, and align with frameworks like CJIS, GDPR, and HIPAA.
What risks arise from improper digital evidence collection?
Improper collection can lead to data loss, corrupted files, broken chain of custody, evidence being ruled inadmissible, or exposure of sensitive data—all of which weaken legal cases and increase liability.
Jump to
You May Also Like
These Related Stories

8 Mistakes an Investigator Can Make When Collecting Digital Evidence
.webp)
10 Ways Digital Evidence Management System Improves Evidence Analysis


No Comments Yet
Let us know what you think