Importance of Digital Evidence Chain of Custody: How It’s Guaranteed
By Ali Rind on January 29, 2026, ref:
Key Takeaways
-
The chain of custody ensures digital evidence remains authentic, traceable, and legally admissible.
-
Digital Evidence Management Systems automate custody tracking from ingestion to courtroom presentation.
-
Features such as immutable logs, encryption, hashing, and role-based access preserve integrity and compliance.
-
VIDIZMO DEMS helps agencies maintain accountability, transparency, and legal defensibility across the entire evidence lifecycle.
In modern digital investigations, maintaining the chain of custody for digital evidence is not just a best practice. It is a legal necessity. Every photo, body-worn camera recording, or surveillance video collected during an investigation must be fully traceable from the moment of capture to its presentation in court. Even a single undocumented access or transfer can compromise evidence integrity and result in inadmissibility.
According to the U.S. Department of Justice, improper handling of digital evidence remains a leading cause of dismissed cases in cybercrime and law enforcement investigations. To mitigate this risk, agencies and enterprises increasingly rely on Digital Evidence Management Systems (DEMS) to maintain a secure, auditable, and automated chain of custody for every piece of evidence.
What Is the Digital Evidence Chain of Custody?
The digital evidence chain of custody is a documented process that tracks how electronic evidence is collected, accessed, transferred, stored, and used. Its purpose is to confirm that evidence remains authentic, untampered, and traceable to its original source throughout its lifecycle.
A proper chain of custody record typically includes:
-
Timestamped logs of every activity
-
Identity of each user accessing the file
-
Device and network details for each access
-
Cryptographic hash values to verify integrity
With electronic evidence, even minor actions such as renaming, copying, or moving a file can raise questions about authenticity. This is why digital evidence management systems must provide secure storage, strict access controls, and complete traceability at every stage.
Why the Digital Evidence Chain of Custody Is Critical
Legal Admissibility
Courts require verifiable proof that digital evidence is genuine and has not been altered. Without a documented chain of custody, evidence can be challenged or ruled inadmissible, potentially undermining an entire case.
Accountability and Transparency
Every interaction with a digital file, including viewing, downloading, sharing, or redacting, must be recorded. This creates accountability among users and ensures transparency during internal reviews and legal proceedings.
Protection Against Tampering
Unauthorized access, accidental modification, or data breaches can compromise evidence integrity. A secure chain of custody minimizes these risks through encryption, access control, and integrity verification mechanisms.
Regulatory Compliance
Organizations handling sensitive or criminal data must comply with regulations such as CJIS, GDPR, HIPAA, and ISO standards. An auditable chain of custody demonstrates compliance and reduces legal and operational risk.
How Digital Evidence Management Systems Guarantee a Secure Chain of Custody
Digital Evidence Management System (DEMS) is purpose-built to preserve digital evidence integrity while simplifying investigation workflows. It guarantees a complete, automated, and verifiable chain of custody through several key mechanisms:
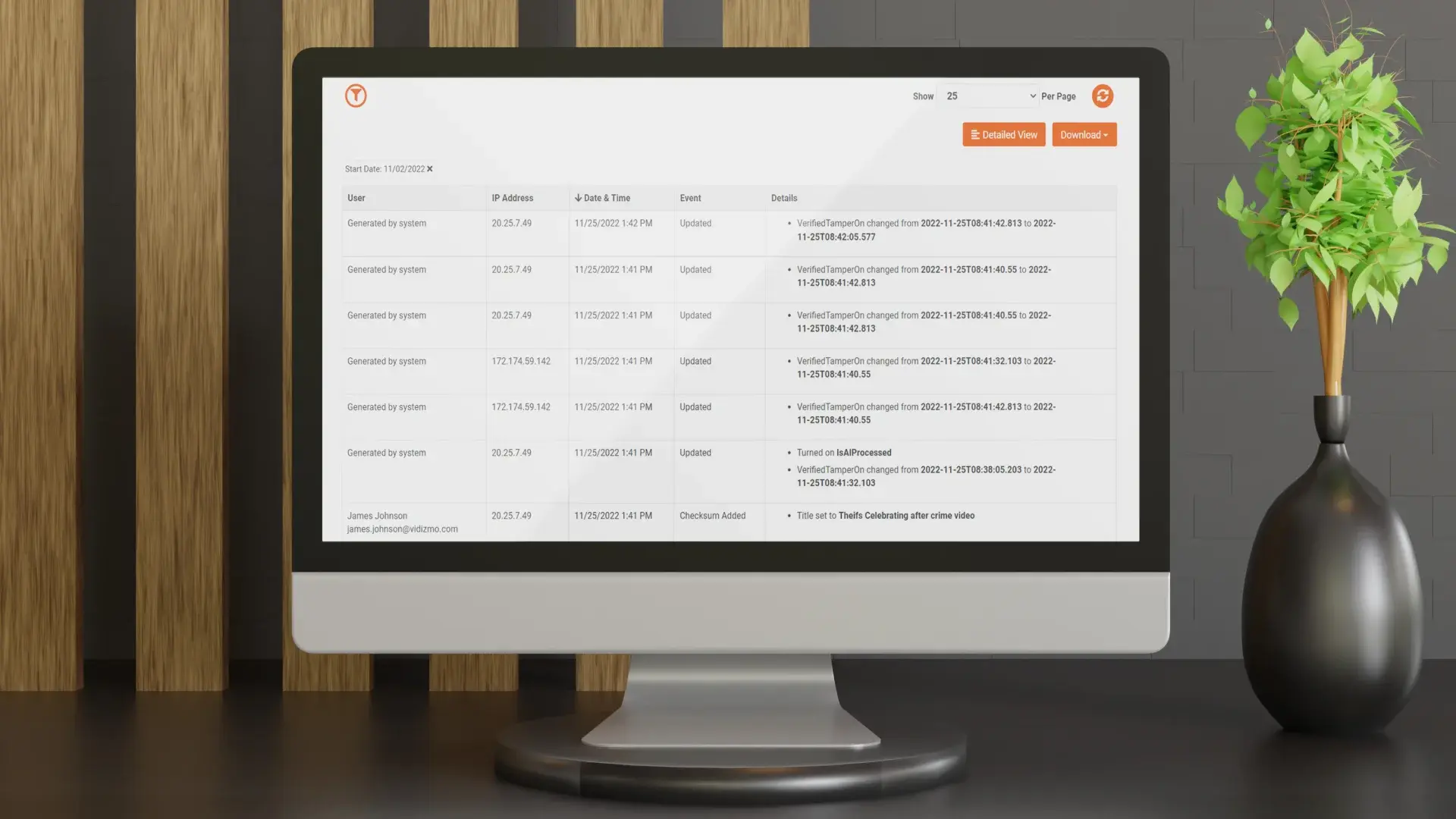
Immutable Audit Logs
Every action performed on a file, including upload, access, sharing, and deletion, is automatically recorded in time-stamped audit logs. These logs are immutable and cannot be altered, ensuring a continuous and defensible record of evidence handling.
Role-Based Access Control
User access is governed by predefined roles and permissions. Only authorized personnel can view, modify, or share evidence, reducing the risk of unauthorized access or accidental tampering.
Cryptographic Hashing for Integrity Verification
Each uploaded file is assigned a unique cryptographic hash that acts as a digital fingerprint. Any change to the file alters the hash value, allowing investigators to instantly verify whether evidence has been modified.
Secure Evidence Transfer
Encrypted data transmission and secure sharing links protect evidence during transfers between investigators, agencies, prosecutors, and legal teams. This prevents interception, leakage, or manipulation during sharing.
Metadata and Case Association
Evidence is automatically tagged with detailed metadata such as uploader identity, timestamps, source device information, and case references. This ensures full traceability and simplifies retrieval during investigations and court proceedings.
Compliance and Audit Readiness
Leading digital evidence platforms are designed to align with CJIS, GDPR, and ISO 27001 requirements. They provide exportable audit logs and reports to support internal reviews, compliance audits, and legal disclosures.
Click to visit the Chain of Custody feature page
Guaranteeing Trust in Every Byte of Evidence
As digital files play a central role in most investigations, maintaining a reliable chain of custody is essential for preserving trust and ensuring fair outcomes. Any gap in documentation or lapse in security can raise doubts about authenticity and weaken a case.
VIDIZMO DEMS provides a secure, centralized, and fully auditable environment that protects evidence from the moment it is collected until it is presented in court or reviewed by stakeholders. By combining controlled access, immutable audit trails, encryption, and integrity verification, the platform ensures that every byte of evidence remains untampered, traceable, and legally defensible.
Experience how VIDIZMO Digital Evidence Management System guarantees complete digital evidence integrity. Contact our team for a personalized consultation or request a demo to explore its capabilities in action.
In today’s world where the majority of investigations involve digital files, maintaining a reliable chain of custody is essential for preserving trust and ensuring fair outcomes. Any break in documentation or lapse in security can cast doubt on the authenticity of evidence, making it unusable in legal or organizational proceedings.
People Also Ask
What is the digital evidence chain of custody?
It is the documented process that tracks how digital evidence is collected, accessed, transferred, and preserved to ensure authenticity and admissibility.
Why is maintaining a chain of custody important?
Without it, digital evidence can be challenged or excluded from court due to potential tampering or mishandling.
How does VIDIZMO DEMS ensure chain of custody?
VIDIZMO DEMS uses immutable audit logs, encryption, cryptographic hashing, and role-based access controls to maintain evidence integrity.
What regulations does VIDIZMO DEMS comply with?
VIDIZMO DEMS aligns with CJIS, GDPR, and ISO 27001 security and privacy standards.
Can evidence integrity be verified in VIDIZMO DEMS?
Yes. Each file is hashed upon upload, allowing integrity verification at any stage of the evidence lifecycle.
Jump to
You May Also Like
These Related Stories

Uncovering the Truth with AI-powered Video Evidence Analysis

The Best Method: Cloud vs. Physical Storage for Digital Evidence




No Comments Yet
Let us know what you think