Role-Based Access Control in Government Digital Evidence Management
By Ali Rind on January 14, 2026, ref:
The uncomfortable truth for many government agencies is this. You likely have more people who could access sensitive digital evidence than people who should. One wrong click exposes a victim, compromises an investigation, or puts a case at risk. And it only takes one.
In an environment where digital evidence spans body worn camera footage, interview recordings, CCTV exports, mobile extractions, and cloud data, old access control models break quickly. Shared drives, generic accounts, manual approvals. None of these stand up to scrutiny when something goes wrong.
Role-Based Access Control in Digital Evidence Management gives you a structured way to decide who sees what, when, and why. It translates legal, operational, and policy requirements into enforceable permissions that actually match how your agency works.
The Risks of Weak Access Control
Before getting into solutions, it helps to be clear about the problem. The risk is not only external breaches. The bigger and more common risk is uncontrolled internal access.
Without Role-Based Access Control in Digital Evidence Management, agencies face issues like:
- Investigators with blanket access to evidence for cases they do not handle
- Supervisors who can modify or delete files without any secondary review
- IT staff able to view sensitive recordings just because they manage storage
- Prosecutors and defense getting evidence through informal, untracked channels
- Contractors and temporary staff retaining access long after projects end
In this reality, every audit, discovery request, or internal review becomes a scramble. You have to piece together who had access to which digital asset and on what basis. Often, the honest answer is that access was broader than it should have been, and the logs are incomplete.
The result. Increased litigation risk, weakened public trust, and operational friction as staff work around rigid or unclear access rules.
Why Government Agencies Struggle with Access Control for Digital Evidence
The public sector access control problem is not a lack of policies. It is a gap between written policies and technical enforcement.
Agencies grapple with several structural challenges.
- Complex organizational structures: Multi agency task forces, joint investigations, and cross jurisdictional operations are common. Static, user by user permissions cannot keep up.
- High staff turnover and role changes: Reassignments, promotions, and rotations happen often. Manual updates to access control lists create delays or leave gaps.
- Mix of sensitive and routine content: Not all digital evidence is equal. Some is public record, some is sealed, some affects officer safety. Treating everything the same is either risky or inefficient.
- Legacy systems and siloed tools: Evidence sits in multiple repositories with different permission models. There is no unified, consistent approach.
- Strict regulatory obligations: Criminal procedure rules, public records laws, privacy regulations, and consent decrees impose specific access and disclosure constraints.
Under pressure, teams often fall back on ad hoc workarounds. Shared credentials. Emailing links. Downloading evidence to local drives. These practices erode chain of custody and open the door to unauthorized access.
This is the gap Role-Based Access Control in Digital Evidence Management is designed to close.
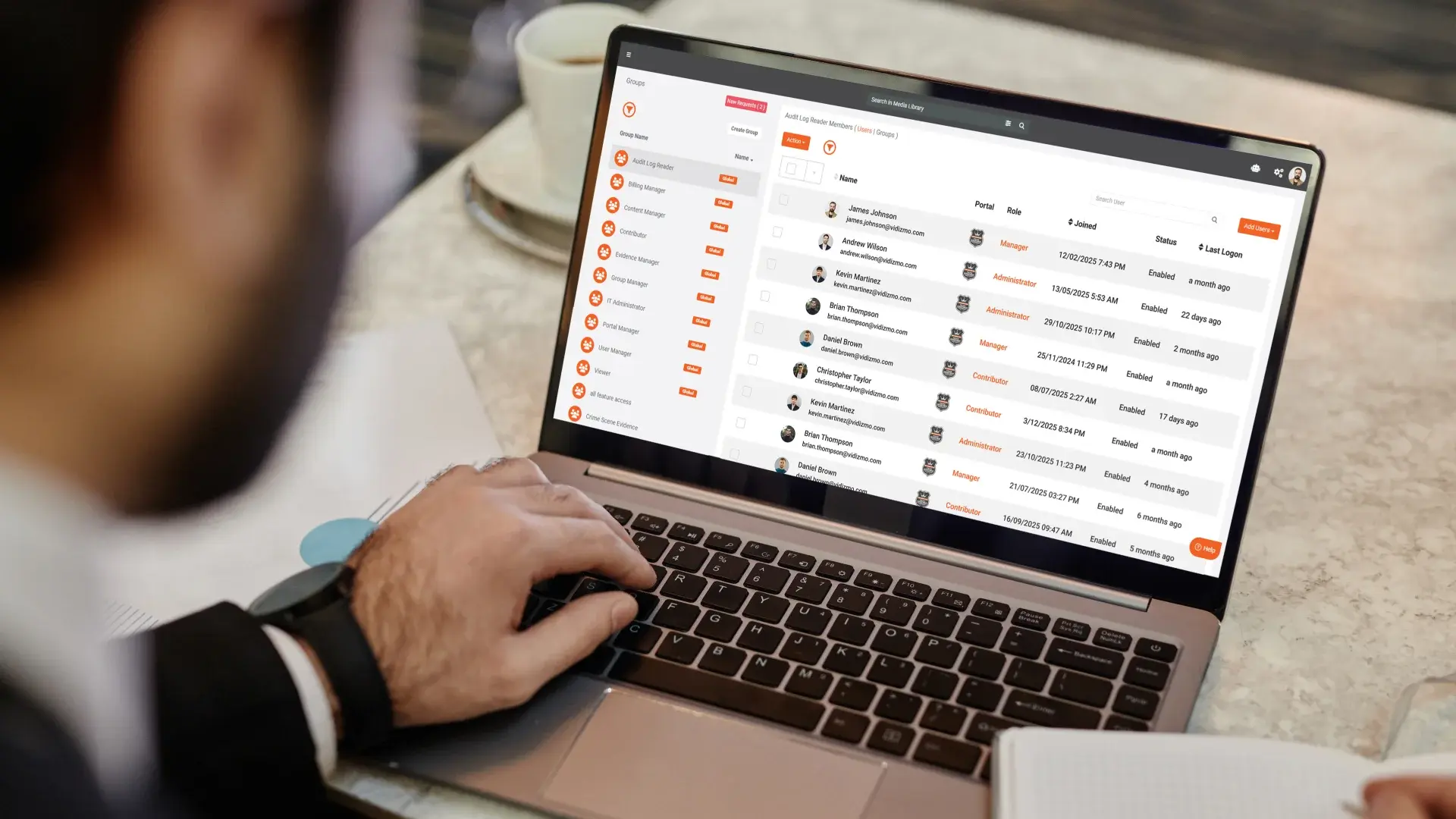
How Role-Based Access Control in Digital Evidence Management Works
Role-Based Access Control in Digital Evidence Management flips the traditional model. Instead of assigning permissions to individuals case by case, you assign users to roles that already have the right set of permissions defined.
At a high level, an RBAC model for digital evidence typically includes.
- Roles: Logical groupings based on job functions, such as Patrol Officer, Detective, Digital Evidence Technician, Prosecutor, Public Defender, Records Clerk, Internal Affairs, System Administrator.
- Permissions: Specific actions a role can perform, such as upload, view, annotate, share, redact, export, approve, or delete evidence.
- Scopes: Boundaries for where permissions apply, such as specific cases, units, divisions, or evidence types.
- Constraints: Rules that further limit access, such as time bound access, supervisor approval for certain exports, or separation of duties for high sensitivity matters.
In practice, Role-Based Access Control in Digital Evidence Management can support scenarios like.
- A patrol officer can upload and view their own body worn camera footage, but cannot see other officers content unless assigned to the same case.
- A detective can view and annotate all evidence linked to their assigned investigations, but cannot permanently delete files.
- A digital evidence technician can process and quality check all evidence, but can only access content in a secure review environment without export privileges.
- A prosecutor can access case evidence shared with their office and can generate controlled disclosure packages with watermarking and access expiry.
- An internal affairs investigator has isolated access to administrative investigations that are hidden from routine operational roles.
Because permissions attach to roles, not individuals, onboarding and offboarding become predictable. You assign the correct role based on position, and Role-Based Access Control in Digital Evidence Management applies the right access controls automatically.
Protecting Chain of Custody with Role-Based Access Control
Chain of custody is only as strong as your ability to prove controlled access. Role-Based Access Control in Digital Evidence Management provides a structured way to demonstrate that only authorized individuals interacted with specific files.
Well designed RBAC supports chain of custody by.
- Enforcing least privilege: Each role receives only the minimum access needed to perform its function. This reduces the number of people who can touch high risk evidence.
- Separating duties: No single role can perform a complete sequence of high impact actions, such as uploading, approving, and deleting the same evidence.
- Driving granular permissions: View, edit, redact, export, and share can be separated. A user may be able to review footage but not export or forward it.
- Enabling case level and file level controls: Access is tied to specific incidents, case numbers, or evidentiary groupings, not to entire repositories.
- Powering comprehensive audit logs: Every access and action is recorded with user, role, timestamp, and context. Logs reflect the RBAC configuration at the time.
When a defense attorney or oversight body challenges the integrity of digital evidence, you can present a clear record. Role-Based Access Control in Digital Evidence Management shows which roles had which permissions, how those roles were assigned, and exactly who exercised which permissions at each step.
Meeting Compliance Requirements with Role-Based Access Control
Government agencies operate under layered regulatory and policy frameworks. These frameworks often specify not only retention and disclosure rules, but also who can access what and under what circumstances.
Role-Based Access Control in Digital Evidence Management provides a technical enforcement layer for compliance mandates such as.
- Limiting access to juvenile, sealed, or expunged records to designated roles only
- Restricting access to evidence involving protected health information to roles with specific training or clearance
- Controlling public records processing workflows and separating request intake from record review and release
- Supporting legal discovery obligations while maintaining confidentiality for unrelated cases
- Enforcing consent decree requirements around supervisory review and accountability
With Role-Based Access Control in Digital Evidence Management, compliance teams can align roles and permissions with statutory language and internal policies. Periodic role reviews then become a focused exercise in confirming that the defined roles still match legal and operational realities.
Best Practices to Implement Role-Based Access Control in Digital Evidence Management
Implementing Role-Based Access Control in Digital Evidence Management is not only a technical project. It is an organizational change that touches policy, training, and governance.
Several practices help agencies succeed.
- Start from real world job functions: Map roles to how people actually work. Interview investigators, prosecutors, records staff, and IT to understand their day to day evidence workflows.
- Define a clear role hierarchy: Use a layered model where base roles cover common functions and elevated roles add narrow privileges. Avoid creating a unique role for every edge case.
- Apply least privilege as a default: Begin with minimal access and open it up where justified. It is easier to expand access than to explain why it was too broad.
- Align roles with case assignment systems: Integrate with case management or RMS where possible, so access to evidence updates automatically when assignments change.
- Separate operations from administration: Limit full administrative privileges to a very small group. Operational supervisors may need elevated access, but not unrestricted system control.
- Implement role review and certification: Schedule regular reviews where managers verify that users still need the roles they hold. Remove dormant or unnecessary role assignments.
- Document and train: Translate RBAC design into simple guidance. Users should understand why they can or cannot access certain evidence and how to request additional access when needed.
Over time, treat Role-Based Access Control in Digital Evidence Management as a living framework. Update roles when laws, policies, or organizational structures change, and verify that any new workflows fit within the defined model.
Access control decisions directly impact evidence integrity and legal defensibility. Book a meeting to see how VIDIZMO Digital Evidence Management System helps government agencies enforce role-based access control across the digital evidence lifecycle.
Common Pitfalls to Avoid with Role-Based Access Control
Even with a solid concept, RBAC projects can falter if certain risks are not managed.
Watch for these common pitfalls.
- Role explosion: Creating too many granular roles makes administration unmanageable. Focus on stable job functions with clear permission sets.
- Privilege creep: Granting temporary access that never gets revoked leads to overly powerful accounts. Set expiry dates for temporary roles.
- Lack of ownership: Without a clear owner, RBAC configurations drift. Assign responsibility to a cross functional governance group that includes legal, operational, and IT stakeholders.
- Ignoring external users: Prosecutors, public defenders, and partner agencies need access too. Design roles for these external parties with constrained, auditable permissions.
- Overriding RBAC through manual workarounds: If workflows are too rigid, staff will find side doors. Monitor for patterns like frequent export to local storage or use of unapproved sharing methods and adjust roles and processes.
By treating Role-Based Access Control in Digital Evidence Management as a core control, not a one time configuration, agencies avoid the slow drift back to ad hoc access.
Key Outcomes of Strong Role-Based Access Control for Government Agencies
When Role-Based Access Control in Digital Evidence Management is well designed and enforced, agencies gain practical, measurable benefits.
- Improved evidentiary integrity: Fewer people can alter or mishandle critical files, and every action is attributable.
- Reduced internal exposure: Sensitive content is limited to a defined set of roles, protecting victims, officers, and bystanders.
- Stronger audit readiness: Clear, role based logs support internal reviews, court challenges, and external oversight.
- Operational efficiency: Staff know what they can access and how. Less time is spent on manual approvals and troubleshooting access issues.
- Consistent compliance: Legal and policy requirements translate directly into enforced access rules rather than informal practice.
- Scalability: As caseloads, data volumes, and partner networks rise, RBAC scales with roles, not one off permissions.
The core shift is from trusting that people will only access what they should, to designing a system where they simply cannot access more than they need.
People Also Ask
What is role-based access control in digital evidence management?
Role-based access control (RBAC) is a security model that limits access to digital evidence based on a user’s job role. Permissions are assigned to roles, and users inherit access only to the evidence and actions required for their responsibilities.
How is RBAC different from user-based access control?
User-based access assigns permissions directly to individuals, which becomes difficult to manage over time. RBAC assigns permissions to roles, making access easier to control, audit, and update when staff change roles or leave.
Why is RBAC important for government digital evidence?
RBAC helps government agencies protect sensitive evidence, maintain chain of custody, reduce insider risk, and meet legal and regulatory requirements by ensuring only authorized roles can access or act on evidence.
How does RBAC support chain of custody?
RBAC restricts who can view, modify, export, or delete evidence and logs every action with role and user context. This creates a verifiable record of evidence handling that supports audits and court proceedings.
Can external users like prosecutors or defense counsel be included?
Yes. RBAC allows agencies to define separate, restricted roles for external users with access limited to specific cases, actions, and time periods, while maintaining full audit visibility.
How granular should roles be in a digital evidence system?
Roles should align with stable job functions such as investigator, supervisor, prosecutor, or records clerk. Granularity should come from permissions and case scope, not from creating many similar roles.
Jump to
You May Also Like
These Related Stories

5 Secure Evidence Storage and Retrieval Software for Law Enforcement

The Complete Guide to FOIA-Compliant Digital Evidence Management




No Comments Yet
Let us know what you think