Understanding CJIS Compliance in Digital Evidence Management
By Ali Rind on January 21, 2026, ref:

Most justice agencies have a CJIS security addendum on file and a policy manual that looks solid during audits. Yet in day to day operations, digital evidence is often scattered across body worn cameras, shared drives, cloud folders, and email attachments. That gap between written policy and actual evidence handling is where CJIS compliance risk quietly builds.
Nothing feels urgent until a discovery request, an internal affairs investigation, or a breach notification deadline arrives. At that point, agencies struggle to answer basic questions: Who accessed a critical video? When was a file modified? Was evidence shared with a third party outside approved channels?
This is not a theoretical concern. Weak CJIS compliance in digital evidence management can lead to:
- Suppression of evidence due to questionable chain of custody
- Increased exposure in civil litigation and wrongful conviction claims
- Negative audit findings when access and activity logs cannot be reconciled
- Loss of public trust after mishandled or leaked digital evidence
The issue is not lack of awareness. Most agencies understand CJIS requirements. The issue is execution: embedding CJIS aligned controls into everyday digital evidence workflows without slowing investigations or overburdening staff.
Why CJIS Compliance is Difficult To Operationalize For Digital Evidence
Most agencies do not fail CJIS compliance digital evidence expectations because they ignore the rules. They fail because their technology stack does not match how cases actually move across units, agencies, and systems.
Typical friction points include:
- Fragmented systems: Body cam, interview room, LPR, and case management all store evidence in silos with inconsistent security controls.
- Informal workflows: Investigators export files to USB drives, burn DVDs, or email links to prosecutors, bypassing official controls.
- Manual logging: Chain of custody is tracked in spreadsheets or paper forms that are rarely complete or current.
- Access sprawl: Broad access groups in Active Directory or local accounts with shared passwords undermine principle of least privilege.
- Ad hoc retention: Evidence is deleted late or early because retention is not automated at the object level.
In this environment, CJIS compliance digital evidence controls become something auditors see in policy documents, not in transactional system behavior. The goal should be different. CJIS should be visible in every evidence upload, view, share, and disposition.
Core CJIS Aligned Controls For Digital Evidence Platforms
To move from policy to practice, digital evidence systems must enforce CJIS requirements by design. At a minimum, platforms should support:
- Comprehensive audit logging across the full evidence lifecycle
- Automated and verifiable chain of custody
- Granular role based access control with least privilege
- Legal holds that override standard retention
- Policy driven retention and defensible deletion
- Secure, traceable evidence sharing
Each of these directly maps to CJIS expectations around access control, auditing, information integrity, and data dissemination.
You might also find our blog on CJIS-Compliant Cloud Evidence Management for Small Police Departments helpful.
Making Chain Of Custody Defensible Under CJIS Scrutiny
Chain of custody is where digital evidence handling faces the most courtroom and audit pressure. Manual signatures and paper logs do not scale for digital files.
An effective digital chain of custody should:
- Automatically create a custody record at ingestion, linking the file to its source, uploader, and case
- Record every access, transfer, and export as a system event
- Preserve original file hashes and verify integrity on export
- Link derivative files, such as redacted clips or transcodes, to the original evidence
- Produce a single, exportable custody report suitable for court
Automated custody tracking reduces staff burden while providing prosecutors with a clear, defensible history of evidence handling.
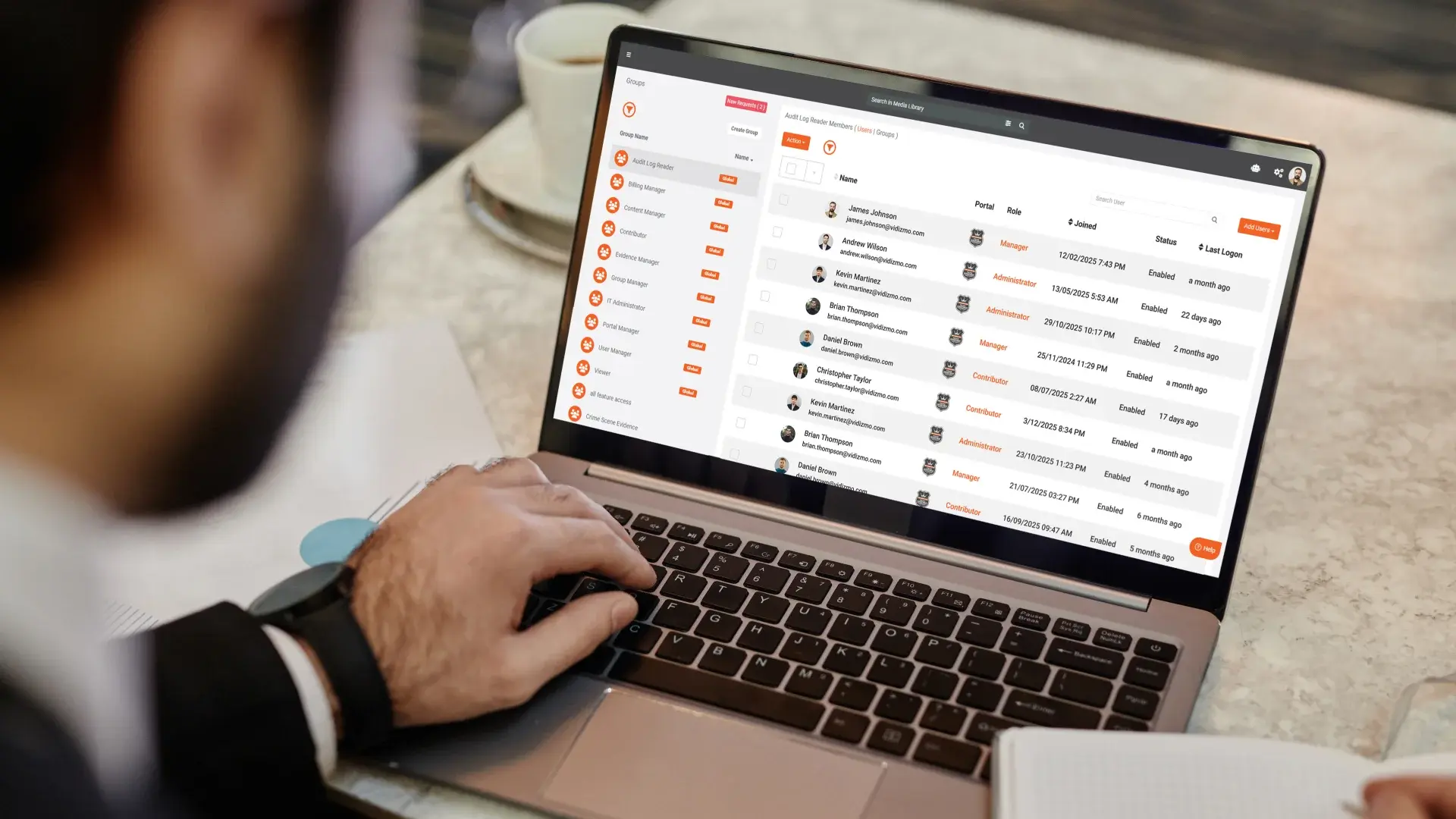
Designing Least Privilege Access For CJIS Governed Evidence
Overly broad access is one of the most common CJIS compliance failures. If everyone can see everything, least privilege does not exist.
A CJIS aligned access model should support:
- Granular roles and permissions for investigators, supervisors, prosecutors, records staff, and administrators
- Case level and incident level access so users only see evidence tied to their assignments
- Group and attribute based access aligned to units, task forces, and jurisdictions
- Time bound access elevation with full audit trails for special investigations
- Federated identity, SSO, and MFA consistent with CJIS requirements
Strong role based access control makes oversharing difficult by default and eliminates reliance on informal agreements.
Legal Holds And Retention Under CJIS Requirements
Retention is where operational pressure often conflicts with CJIS compliance digital evidence expectations. Storage costs rise, cases linger, and someone decides to manually clear old files without a formal policy trail.
A compliant approach requires two components that work together.
Legal Holds For Digital Evidence
Legal holds ensure evidence is preserved regardless of standard retention rules. Platforms should allow agencies to:
- Apply holds at the case, folder, or individual evidence level
- Record the reason, owner, and effective date of each hold
- Prevent deletion or modification while the hold is active
- Audit all changes to hold status
This creates a defensible record when courts or oversight bodies question why evidence was retained or deleted.
Policy Driven Retention Management
Retention policies must reflect state law, records schedules, and litigation risk. Systems should support:
- Retention rules by evidence type, source, or case category
- Policy enforcement at ingestion, not retroactively
- Approval based disposition workflows with audit trails
- Secure deletion that proves data is no longer accessible
Proper retention management reduces risk while supporting CJIS auditability and public records obligations.
Book a meeting to review your digital evidence workflows and discuss how CJIS aligned controls can be applied in practice.
Secure Evidence Sharing Without Breaking CJIS Compliance
Evidence routinely moves beyond a single agency. Each handoff introduces risk if sharing relies on downloads, email attachments, or consumer cloud tools.
CJIS aligned sharing workflows should include:
- Controlled, expiring access links
- Recipient authentication before viewing
- Permission scoping such as view only or download restrictions
- Full logging of recipient access and activity
- Support for interagency and cross jurisdiction sharing
Secure sharing replaces unmanaged copies with controlled access, which is essential for CJIS compliant evidence dissemination.
Key Points
-
CJIS compliance risk in digital evidence comes from the gap between written policy and daily evidence handling practices.
-
Scattered storage across body cameras, shared drives, cloud folders, and email increases the likelihood of audit failures, discovery issues, and evidence mishandling.
-
CJIS compliance failures are usually caused by execution problems such as manual workflows, fragmented systems, broad access, and informal sharing, not lack of awareness.
-
Digital evidence platforms must enforce CJIS aligned controls by design, not rely on user behavior or after-the-fact documentation.
-
Automated chain of custody is essential to prove evidence integrity, access history, and defensible handling in court and audits.
-
Role based access control with least privilege reduces oversharing and limits exposure by ensuring users only access evidence tied to their role and cases.
-
Legal holds must override standard retention rules to preserve evidence during litigation, investigations, or oversight actions.
-
Policy driven retention and defensible deletion lower risk while supporting CJIS auditability and records compliance.
-
Secure evidence sharing should replace email attachments and unmanaged downloads with controlled, traceable access.
-
CJIS compliance should be evaluated through real system behavior such as audit logs, access enforcement, and sharing workflows, not vendor checklists.
How To Evaluate Digital Evidence Platforms For CJIS Alignment
CJIS compliance should be evaluated at the control level, not through marketing claims. When reviewing platforms, ask vendors to demonstrate:
- A complete audit log for a sensitive case, including views, exports, and shares
- Automated chain of custody from ingestion through disposition
- Role based access models that reflect real agency structures
- Creation, enforcement, and release of legal holds
- Retention policies and defensible deletion workflows
- Secure sharing with external prosecutors under CJIS controls
The goal is to see how controls behave under real workloads, not how they appear in documentation. The more compliance is embedded in the system, the less risk accumulates through manual workarounds.
People Also Ask
How Does CJIS Apply To Digital Evidence Platforms?
CJIS governs systems that store or process criminal justice information. Digital evidence platforms handling case related media fall within scope and must meet CJIS requirements for access control, auditing, encryption, and incident response.
What Are The Most Common CJIS Gaps In Digital Evidence Workflows?
Incomplete audit logging, weak access controls, unmanaged sharing, manual custody tracking, and inconsistent retention are the most common gaps.
Is Encryption Alone Enough For CJIS Compliance?
No. Encryption is necessary but insufficient. CJIS also requires identity management, access control, auditing, training, and documented procedures.
How Should Agencies Share Evidence With Prosecutors?
Agencies should use secure portals or controlled access links with authentication, expiration, and logging. Email attachments and unmanaged transfers should be avoided.
How Long Should Digital Evidence Be Retained For CJIS Compliance?
CJIS does not mandate specific retention periods. Retention should align with state law, records schedules, and litigation risk, supported by policy driven automation.
Jump to
You May Also Like
These Related Stories

Legally Collecting Digital Evidence: Rules and Best Practices
Role-Based Access Control in Government Digital Evidence Management




No Comments Yet
Let us know what you think